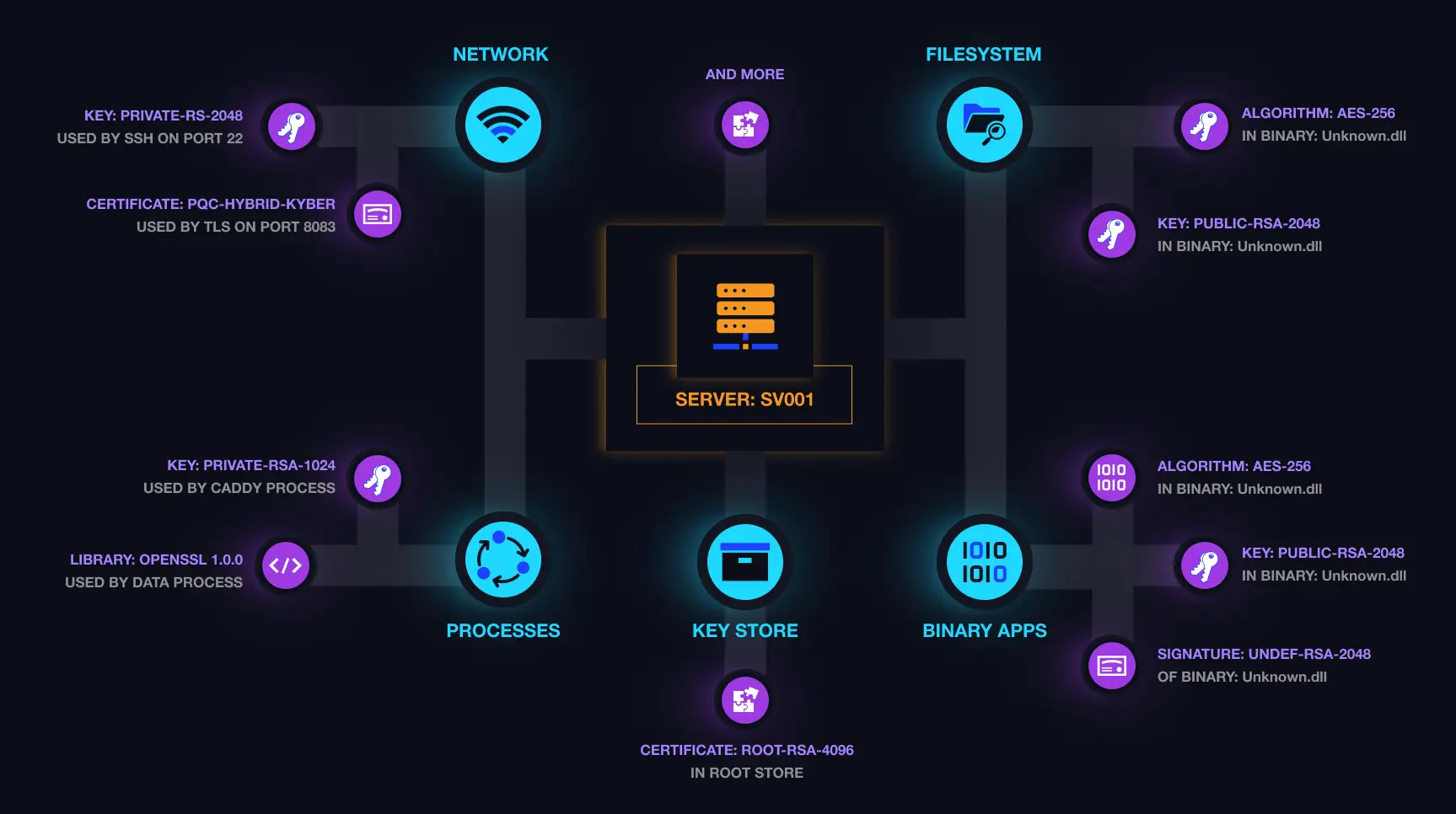
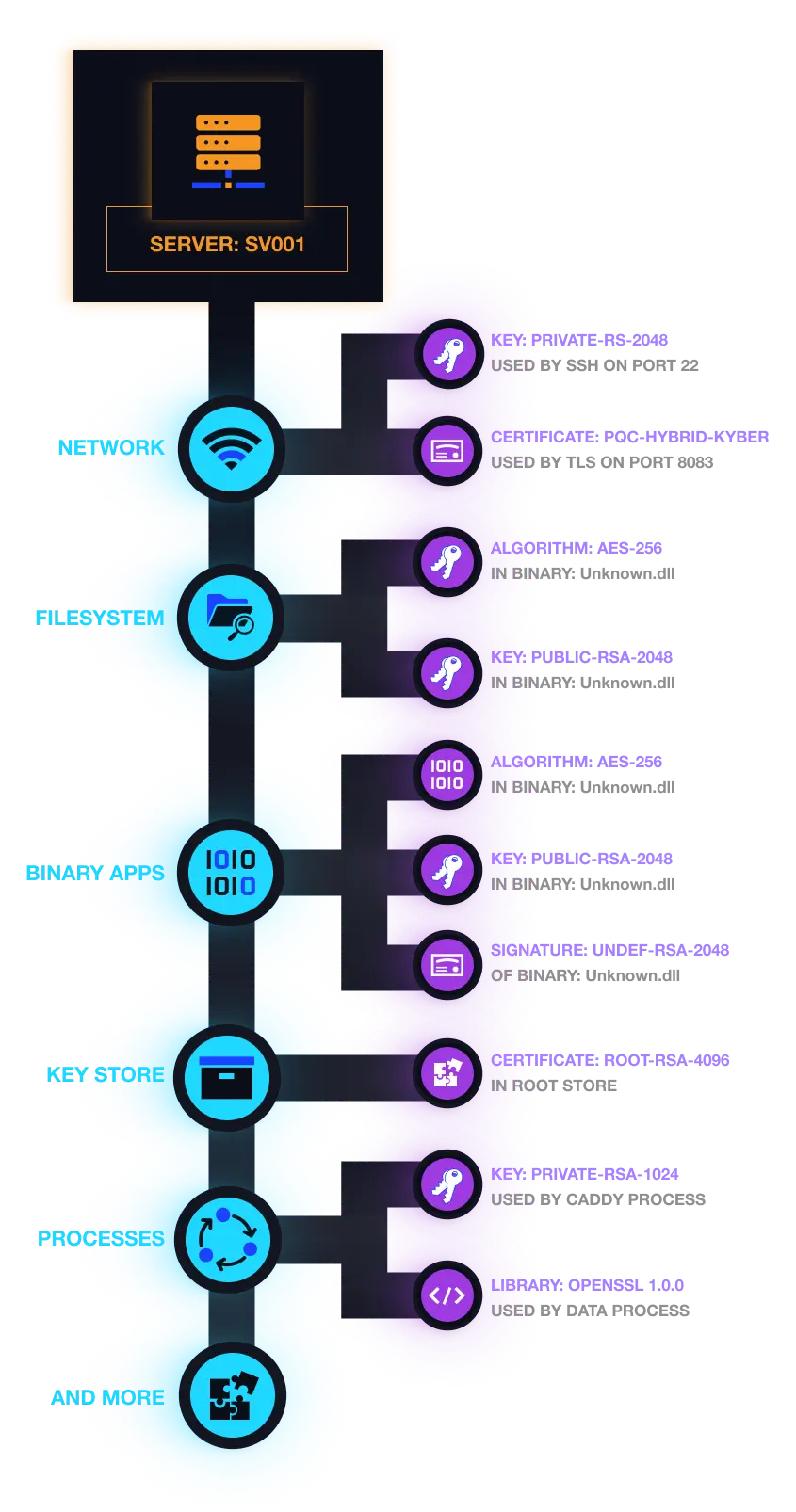
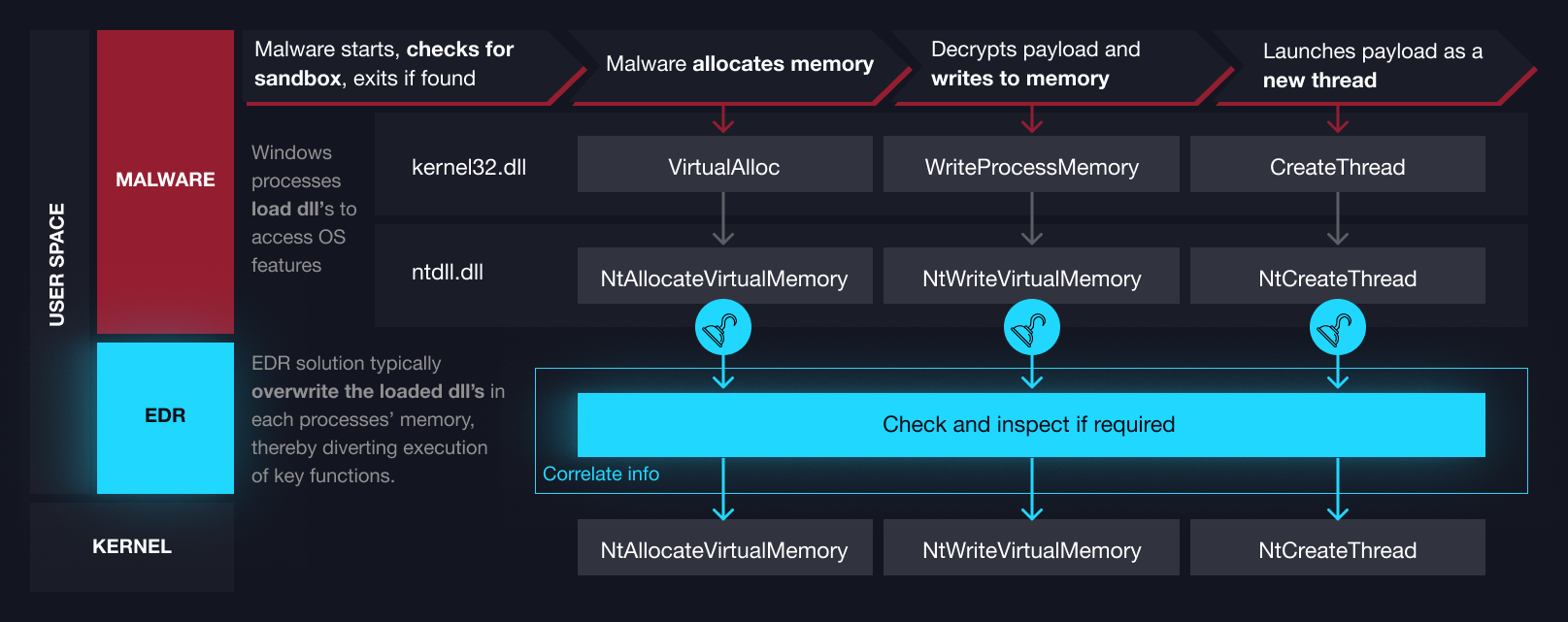
Featured
Innovations
We don’t make cyber. We make cyber better.
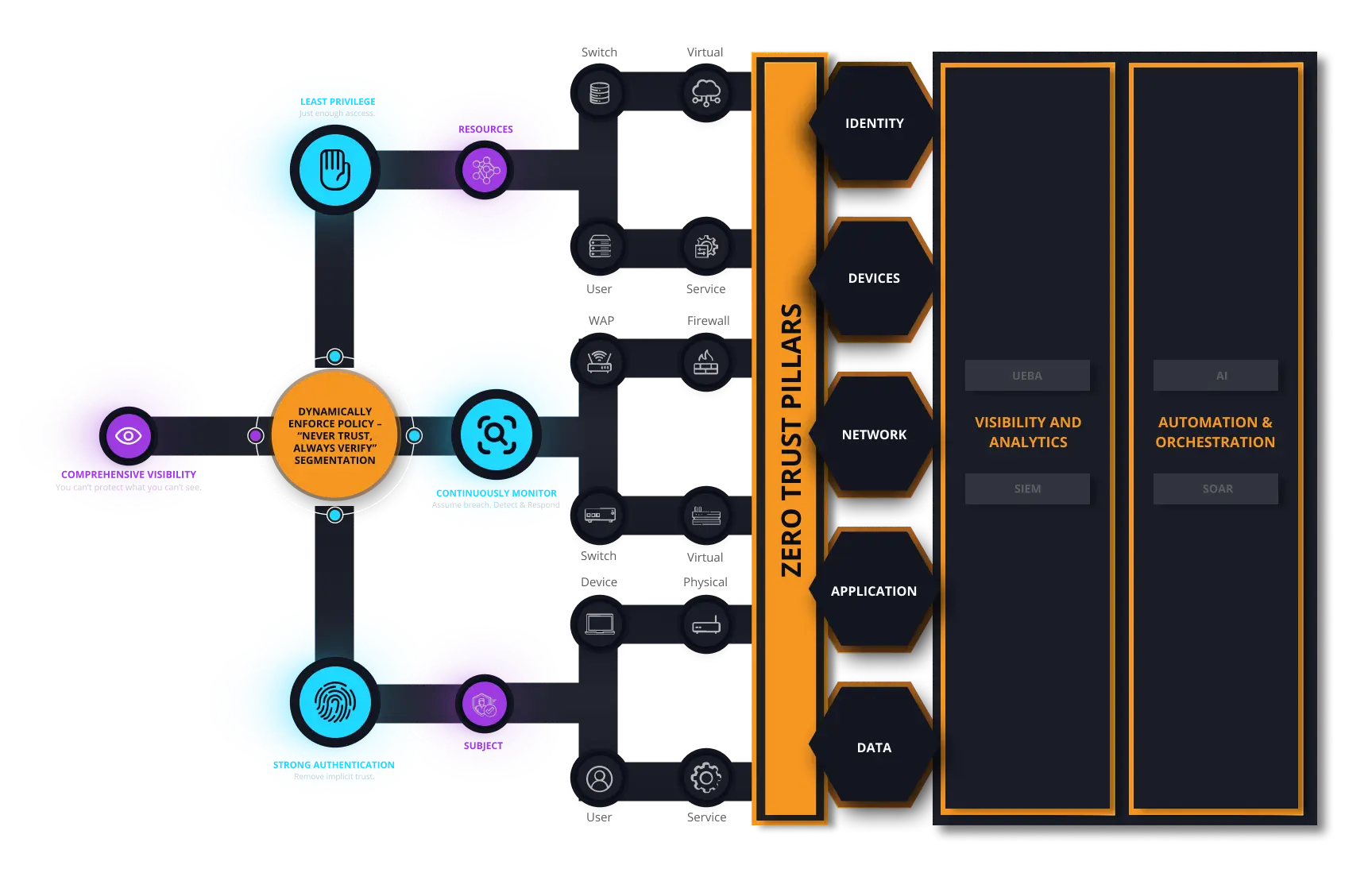
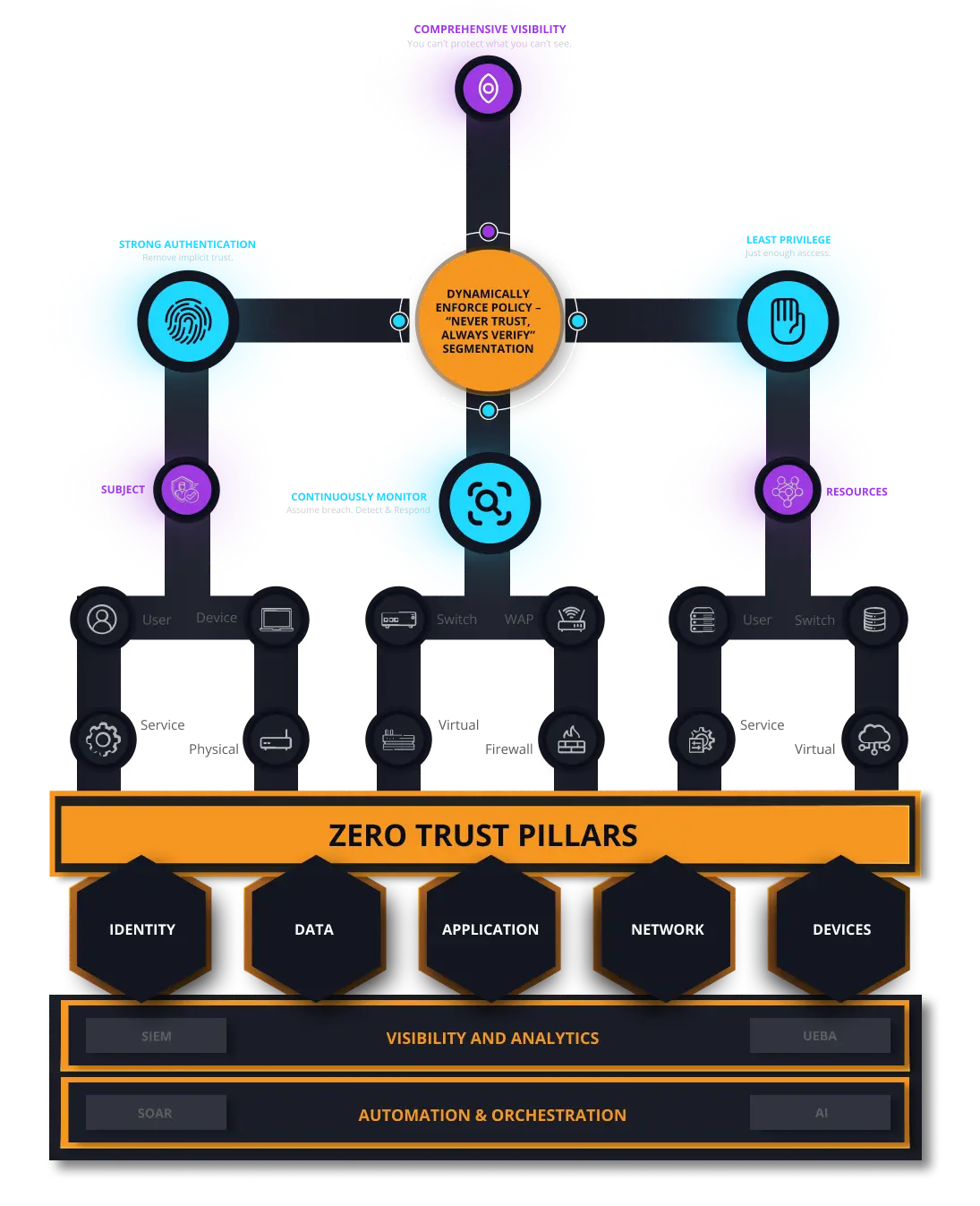
In a Zero Trust world, who do you trust? We tackle the most complex cyber challenges and advance Zero Trust maturity for organizations by introducing new use cases and innovations that bring together best-in-class solutions with groundbreaking emerging technologies. By working together, we not only provide end users with truly unique use case solutions, but we also make essential innovations more readily accessible to those who need them most.